Data is undoubtedly the backbone of most modern businesses. As business goes increasingly digital and into the cloud, so the amount of data that businesses must manage and control grows and grows in scale and complexity. Data management that is proactive and effective is therefore central to any business today, however small. It is for that reason that systems that prevent and address data breach occurrences are increasingly important.
Central to the preservation of your company’s data, in all its forms and permutations, are your employees. They are the ‘frontline’ in your attempt to secure your company data, given that they are often the ones who access data, work with it, manage it, modify it, pass it on or share with others, and so forth. Therefore, they need to know how to prevent data breach events. This requires knowledge and skills that need to be trained. This article will provide a 4-step approach as to how you can train your staff to help prevent data breaches.
Step 1: Understanding Data Breaches
First and foremost, your employees need to understand exactly what is meant by the term ‘data breach’. According to leading online security company Kaspersky, a data breach is the exposure of a company’s confidential, sensitive or protected information to an unauthorized person. In the breach, files are viewed and/or shared without the permission of the data owner. Furthermore, a breach can either be active (for example, an aggressive, planned cyberattack by a hacker) or passive. An example of the latter could be a lapse in existing security protocols due to an employee using the same weak password for all their company accounts that is easily breached.
Data breaches can occur due to lost or stolen devices or computer hardware, or they can be the result of a benign (accidental) or malicious action by someone within an organisation (i.e. an ‘insider event’). Furthermore, data breaches can occur in many different guises, resulting in the loss of sensitive, proprietary or confidential information. This can range in everything from compromised server or individual account passwords and private customer data, to stolen corporate credit card numbers, trade secrets, confidential strategy plans, product blueprints or any number of other types of data that a company wishes to protect.
Step 2: Understanding the Potential Cost
Employees need to understand just how dangerous cyberattacks, security lapses or other breaches in data can be for a company. This knowledge will be sobering for most employees given that they probably don’t realize just how costly said breaches can actually be.
Data breach costs went up dramatically in 2021, with a global average cost of $4.24 million (roughly £3.03 million) per incident. The cost of data breaches in the UK was above the global average, with the average cost in the UK rising by 8% compared to 2020 to £3.36 million per incident, although the United States remains the country with the most expensive data breaches. The numbers were the highest recorded in the 17-year history of IBM’s annual report on data breach costs, as based in 2021 on 537 breaches across 17 countries and 17 industries.
Statista released UK statistics regarding data breaches, in which the high cost of breaches for all businesses, including SMEs, can be clearly seen in the graph below:
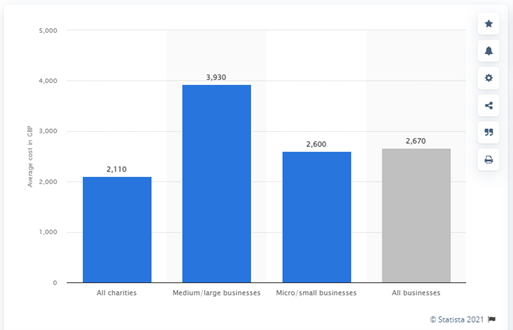
The reason for this dramatic rise in data breaches? A sharp increase in employees working remotely certainly has made companies more vulnerable to data attacks.
Step 3: Practical Measures
Once employees are well aware of all that constitutes a potential data breach, and how costly a breach can be, they then need to be trained on practical actions they can do in order to protect the company’s data. They need to be trained on how to avoid, for example, phishing emails, often with embedded links, that can gain unauthorised access to your company’s entire server. Phishing remained by late 2021 the most popular method or ‘back-door’ used by unfriendly entities to breach company data.
Other examples of popular social engineering ploys used to breach company security include SMS and spamming campaigns that use sometimes highly sophisticated and manipulative emotional and psychological tactics to gain access to company systems and confidential information, as well as personal information. Employees should also be taught safe Wi-Fi usage habits, particularly when working in public places such as coffee shops and airports, and even from home. They should also be taught the ‘magic four words’: Keep Your Devices Close.
Sometimes the simplest measures are the best, and in in this instance the key word is passwords. Employees need to be trained (rather, drilled!) on the importance of password security practices. These should include making passwords as complex as possible, although there is the danger that overly complicated passwords can be forgotten. A better gambit is to highlight the importance of changing passwords on a regular basis. And, at the least, stressing the importance of having passwords with a combination of upper-case and lower-case letters, numbers and special symbols.
Furthermore, there needs to be strict adherence by every employee to a company’s policies regarding data retention. These policies should encompass the secure destruction of data (whatever its format), be it documents/data in digital or physical formats. This destruction of all data should ideally be done by a certified, reputable data destruction service , so as to ensure the thorough and verifiable security thereof.
Need to include details about adherence to Data Retention policies, and ensure that both physical and digital information are securely destroyed. Whether this is through using 3rd party data destruction services, companies and employees must take responsibility for data in their possession.
Step 4: Emphasizing Alertness
Employees need not only be ‘guardians’ of data, i.e. trained to ensure that they know how to do everything in their own domain to protect data. They can also act as ‘police’ of internal data, whereby they are trained to be actively vigilant to be on the lookout for possible/pending or active breaches regarding data. Their role in this regard can be invaluable, since time can be a huge enemy in data losses.
Consider this: A ‘breach life cycle’ is the amount of time that lapses between a data breach first occurring and its complete containment. According to IBM, globally the average breach life cycle in 2019 was 279 days, comprising 206 days to identify a breach and 73 days to successfully contain it. That average number went up in 2021 to 287 days, with 212 days needed to identify a breach and 75 days to contain it. It is gradually taking longer to both identify and contain data breaches. It’s logical that each passing day can mean further operational detriment and loss of revenue for a company. Therefore, having employees as ‘data-savvy’ guardians and police of company data can only be beneficial.
Employees must be considered as an integral, if not central, aspect of your company’s data protection system. No amount of expensive IT security measures will prevent data breaches due to the data-related actions (or inactions) of inattentive or poorly-trained employees.
In the end, all it can take is just one employee to completely flounder your data security. The result could be financially devastating for your company. That chilling possibility should be reason enough to train every single employee on the importance of sound, secure data usage.